The Honeypot:
I got bored so I made a very basic Honeypot (A server designed to lure attackers in order to study their behaviour) and thought it would be fun to document the process and upload the results!
~~~~~~~~~~~~~~~~~~~~
I decided to make a non-interactive server that hosts a fake SSH server, in order to capture data that potential hackers input in order to try and gain access.
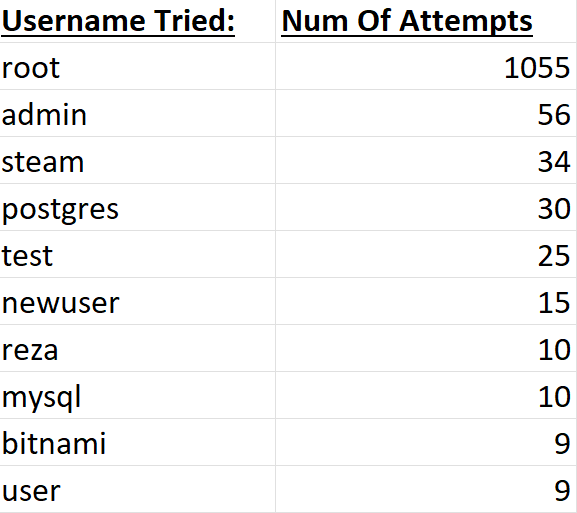
These are usually automated scripts that hackers leave running that attempt a wide range of common passwords to gain access to unconfigured or new servers. By default, SSH does not limit the amount of login attempts you can make, so these hackers can try hundreds or thousands of different passwords
This is why it's important to never use default passwords for anything and to make sure your passwords are strong and complex!
~~~~~~~~~~~~~~~~~~~~
I've tried to include links to all resources I used to set this up but let me know if I missed anything